CTF Writeup: Babybof1 Pt2
The Problem Description:
Ghidra Decompilation:
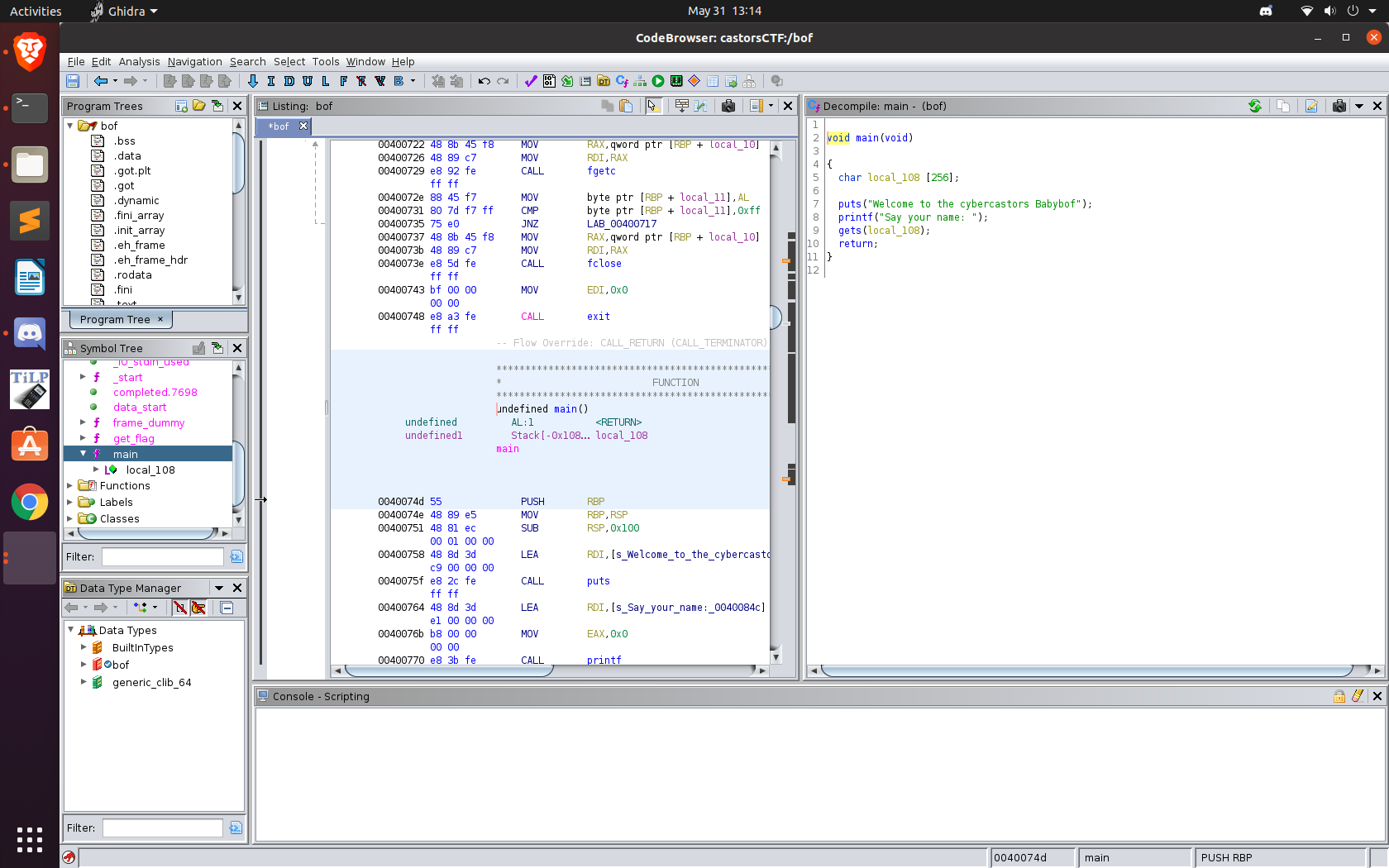
As we can see from the above decompilation, the vulnerability in the program is gets().
The call to gets() doesn’t check to make sure our input will fit into the buffer we give it,
so we can write past the length of the buffer, leading to a classic buffer overflow vulnerability.
The gets() means we the input can contain any character, even \x00, except for newlines.
Let’s check what kind of binary we have and what protections it has.
The binary is a 64 bit ELF binary.
- Partial RELRO (Relocation Read-Only): PLT GOT entries are still writeable.
- No canary: We can safely overwrite the saved return address without worrying about overwriting a stack canary.
- NX disabled: The stack is executable, so we could use shellcode if we wanted.
- No PIE: No ASLR in the binary itself, so addresses of functions like main will remain constant. However, the actual machine we run the binary on still will probably have ASLR enabled which means the stack addresses will change.
First I tried using shellcode, but since ASLR is still enabled on the machine, the stack addresses will be randomized.
This means that the address of the input buffer will change. I didn’t know how to overwrite the return address with the correct address of the shellcode, so I just decided to use ret2libc. (Note: I think using shellcode was the intended solution and not ret2libc).
Libc is a standard C library with all sort of useful functions. A ret2libc attack can take advantage of functions like system() in libc to spawn a shell.
The first step is to determine how much input we need to overwrite the return address.
The stack should look like this for main().
[ Saved Return Address ]
[ Saved Frame Pointer (EBP) ]
[ Buffer[255] ]
[ Buffer[254] ]
[ Buffer[253] ]
. . . . . . . .
[ Buffer[2] ]
[ Buffer[1] ]
[ Buffer[0] ]
We want to write past the buffer, overwrite the saved fram pointer, and then overwrite the saved return address our own address to our exploit.
We know that the buffer is 256 bytes from Ghidra, so we can use the following to test how much padding we need until we overwrite the return address.
In the diagram above, writing to buffer will make input go “up” the stack.
We receive a segfault when we the binary with our input. It seems we stop at the ret instruction in main.
A ret instruction is like pop rip, so let’s what the ret instruction was trying to get from the stack.
It looks like the program was trying to return to the address 0x4343434343434343 which is probably why we got a segfault.
Since 0x43 is an ascii C, we know that the stack will look like this after gets() is called:
[ Saved ret CCCCCCCC ]
[ Saved EBP BBBBBBBB ]
[ Buffer: A*256 ]
Now we just have to replace CCCCCCCC with the address of our exploit. We’ll use a ROP (Return Oriented Programming) Chain to accomplish this.
Ret2libc
I used this as a template for my 64-bit ret2libc attacks. Check the post out since it explains the basics of ret2libc pretty well.
Leak Libc
First we need to leak a libc function address. ASLR is enabled on the machine, so the address of libc functions will be randomized. In order to know the address of system() and other libc functions, we need to first find the base address of libc.
We can use puts or printf to leak the address of a libc function. Puts is easier to use though, so we’ll use that in this challenge.
We’ll be leaking the address of the __libc_start_main function and then subtracting the offset to calculate the base of libc. Then using the base of libc we can calculate where system() and the “/bin/sh” string is.
Here’s our ROP chain:
[Address of pop rdi, ret] [Address of __libc_start_main entry] [Address of puts]
64-bit calling conventions say that the first argument of a function should be in the rdi register.
So our rop chain will put the address of the __libc_start_main entry into rdi and then call puts, printing out the address of __libc_start_main.
This is what the stack will look with our ROP chain:
[ Address of puts ]
[Address of __libc_start_main entry]
[ Address of pop rdi, ret ]
[ Buffer: A*256 ]
Here’s our script to leak __libc_start_main:
Let’s run the script:
We see that for this particular run, the address of __libc_start_main was 0x7fd7206d3fc0.
We need to find out what version of libc is running on the server since different versions have different offsets between the base and functions.
Luckily there’s a tool that finds the right libc version for you based on the address of a libc function.
Download the database and tools here and then run the following:
This shows us that the server was using the libc6_2.31-0ubuntu9_amd64 version. We can use download libc6_2.31-0ubuntu9_amd64 to download that libc version.
Note: There is also an online libc database at https://libc.blukat.me/, but it only works sometimes since its database probably isn’t as comphrehensive.
Exploit
We can use the pwntools python library to find libc offsets.
This calculates the base libc address by subtracting the offset from __libc_start_main
Then by using this libc base address we can find the addresses of system() and “/bin/sh” to spawn a shell.
Using pwntools:
For our exploit, we need to be able to call main() twice: once to leak libc and another time to call system().
We can just append the address of main() to our first ROP chain to accomplish this.
First ROP chain:
Then our second rop chain will call system:
Combine the above into a script:
Run the script:
Note: during the actual ctf, there was a weird buffering issue, so I had to run exploit_buf.py around 100 times to get a shell.
Towards the end of the ctf, the organizers fixed the buffering issue, so running exploit.py just once will now work.
Also if you see any inaccuracies anywhere, feel free to contact me!
2020-06-16 00:58 +0000 (Last updated: 2020-12-06 03:31 +0000)